Nowadays, mobile apps for supply chain play a crucial role in enabling individuals and organizations to handle their inventory and supply chain operations easily.
Organizations need mobile apps for supply chain development that meet the needs of customers, partners, and employees to remain relevant, responsive, and successful.
However, development can seem intimidating. When choosing operating systems and platforms, you need to account for mobile device limitations and potential app delivery challenges. With the mobile apps for supply chain development organizations increasing their security measures, attackers have been forced to innovate. Code reuse and the cloud-native approach have given attackers new ways to mount attacks several steps away from their targets. Vulnerabilities allow threats to infiltrate the supply chain, steal sensitive data, compile malware, and gain control of the system.
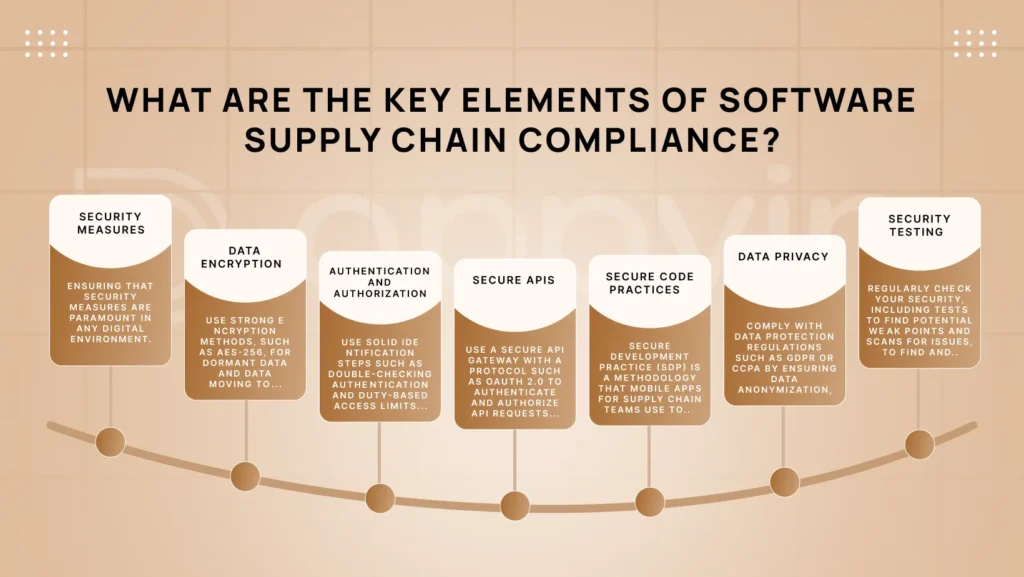
What are the key elements of software supply chain compliance?
Security Measures:
Ensuring that security measures are paramount in any digital environment. From data privacy to authentication protocols, sensitive information must be protected against potential threats. Implementing safe regulatory practices and regular security testing further strengthens the system against vulnerabilities. Staying alert and ahead in handling security issues helps companies keep their data and systems safe. This way, they shield themselves from dangerous online threats and breaches.
Data Encryption:
Use strong encryption methods, such as AES-256, for dormant data and data moving to keep private details safe from prying eyes. Employ strong encryption schemes for both traveling and dormant data. However, sophisticated encryption codes mean that even if unapproved access happens, the information stays indecipherable.
Authentication and Authorization:
Use solid identification steps such as double-checking authentication and duty-based access limits in the mobile apps for the supply chain. This helps confirm who users are and only lets them get to resources if it matches their job and duties in the supply chain.
Apply this two-step checking process and job-based access limits to make sure people are who they say they are. This also stops access depending on their set roles and rights. Doing this helps stop people without permission from messing with important info.
Secure APIs:
Use a secure API gateway with a protocol such as OAuth 2.0 to authenticate and authorize API requests. Implementing strict access controls and amount limiting mechanisms adds an additional layer of protection against malicious attacks targeting APIs. Follow best practices for authentication, IP whitelisting, rate limiting, input verification, and secure communication protocols when developing APIs to prevent unauthorized access, and other vulnerabilities.
Secure Code Practices:
Secure development practice (SDP) is a methodology that mobile apps for supply chain teams use to integrate security into every stage of mobile app development.
Organizations use best practices in secure development, such as code review, threat modelling, implementing a secure app development policy, and using a security software development framework. By implementing secure development practices, development teams can identify security vulnerabilities early in the development lifecycle of software systems. Moreover, this significantly reduces the time and effort required to secure these systems.
Data Privacy:
Comply with data protection regulations such as GDPR or CCPA by ensuring data anonymization, pseudonymization and user consent mechanisms are in place. Clear privacy policies and robust data governance structures build user trust and confidence in your application. Comply with data privacy laws, anonymize or rename sensitive data where possible, and minimize data collection to minimize the risk of a data breach and hit the beneficiary to protect user confidentiality.
Security Testing:
Regularly check your security, including tests to find potential weak points and scans for issues, to find and fix any security problems before they become serious issues.
Security audit tools, tried and tested by skilled security teams, can highlight known issues. Consequently, regular security checks, penetration tests, and audits by proven professionals or respected companies can help spot and tackle possible vulnerabilities in the app.
Scalability Strategies:
Scalability strategies are important for businesses to drive scalability and increased demand while maintaining optimal performance. Cloud infrastructure provides flexibility and scalability, allowing organizations to scale things up or down as needed. Microservice architecture enables modular and independently scalable components, facilitating agility and scalability. However, horizontal scaling involves adding more instances to existing resources to divide the workload and increase efficiency.
Database scaling ensures that data storage systems can efficiently handle increasing volumes of information. Caching and content delivery networks (CDNs) optimize content delivery and improve scalability by reducing latency and improving user experience Monitoring and auto-scaling mechanisms continuously monitor performance metrics and automatically update resources to meet demand changes addressed to ensure scalability. Implementing these scalability mechanisms enables organizations to adapt to changing business needs and drive growth to keep going smoothly.
Cloud Infrastructure:
Leverage cloud computing platforms like AWS, Azure, or Google Cloud to advantage of elastic infrastructure sources and pay-as-you-pass pricing fashions. Additionally, cloud services offer scalability functions inclusive of vehicle scaling, load balancing, and worldwide availability zones, ensuring optimum overall performance even throughout top site visitor durations.
Microservices Architecture:
Adopt a microservices structure in which utility components are decoupled and independently deployable. This modular method helps horizontal scaling by permitting man or woman offerings to scale primarily based on demand, as opposed to scaling the entire monolithic software.
Horizontal Scaling:
Scale horizontally by adding more instances of application servers or microservices to distribute the workload frivolously. Additionally, container orchestration platforms like Kubernetes simplify the management of containerized packages and allow automatic scaling primarily based on predefined metrics like CPU usage or request throughput.
Database Scaling:
Implement scalable database solutions together with sharding, replication, or NoSQL databases to address growing information volumes and transaction throughput. Distributed database systems like Amazon Aurora or Google Spanner provide high availability and scalability without sacrificing fact consistency.
Caching and Content Delivery Networks (CDNs):
Cache frequently accessed records at numerous layers of the software stack to lessen latency and enhance responsiveness. CDNs distribute static belongings like photos, scripts, and movies throughout geographically dispersed issue servers, minimizing the impact of latency on character experience.
Monitoring and Auto-scaling:
Use monitoring tools such as Prometheus or Datadog to monitor key performance metrics such as CPU usage, memory usage, and response time in real-time.
Moreover, establish automatic scaling processes to dynamically adjust resource allocation based on business processes, and verify efficiency and cost-effectiveness.
Use robust analytics and robust auto-scaling capabilities to deliver release resources based on predetermined demand and scaling policies, aligning resources with real-time demand.
Conclusion
In summary, supply chain management deals with the supply and demand of goods and services. A mobile app for supply chain management helps in this task. However, supply chain management requires a relationship between supply and demand.
Moreover, it covers all stages from manufacturer to supplier, supplier to logistics, warehouse, warehouse to retailer, and retailer to customer. By prioritizing security and scalability, organizations can design flexible and future-proof supply chain management systems that protect critical data, and drive productivity. It also adapts to business-increasing numbers and user requirements to support growth and success in the digital age.